Network Analysis with Wireshark
Unveiling Packet Dynamics and Security Measures
Conducted hands-on packet analysis using Wireshark to examine network vulnerabilities. Captured and filtered 11,000+ packets to:
• Compare secured (HTTPS) vs. unsecured (HTTP) traffic flows
• Demonstrate phishing risks by reconstructing TCP streams containing exposed plaintext data
• Identify suspicious device communications through conversation analysis
Key Technical Processes:
Applied display filters (tcp.analysis.flags, port 80/443) to isolate SYN handshakes and protocol traffic
Revealed security weaknesses by intercepting simulated HTTP login data
Documented methods to hide protocols and detect anomalous device communications
Analyzed packet structures across all OSI layers for threat indicators
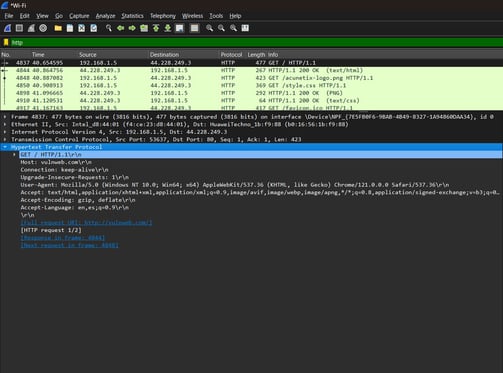
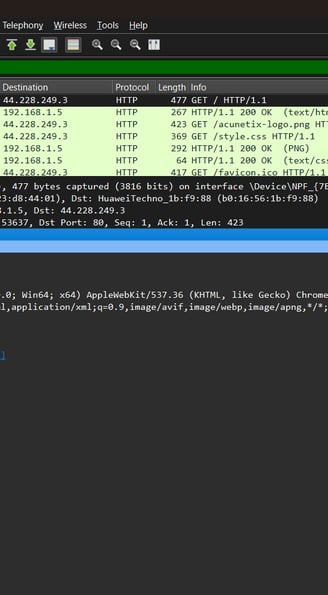
Viewing packet contents for the HTTP

